Table of Contents
Untraceable
See our Youtube promo video at: https://www.youtube.com/watch?v=KFwP8UetQ0s
Members:
Chris Elcombe:
A 4th year Digital Media student at York University. Previous work has been mainly done in user interface and user experience design, gesture and motion tracking, and educational technologies with a focus on students with exceptionalities. Co-author of Gestural Learning http://gl.aseerimedia.com/, a gesture input system for the computer with a focus on students with exceptionalities (currently in publishing process) and co-creator of In the Key of C, a motion tracking music piece, part of Nuit Blanche 2014.
Patrick Reding:
A 4th year Digital Media student at York University, he has previously earned a Bachlor of Mathematics, Double Honours in Computer Science and Mathematics from Carleton University in 2003. His primary interest is in games, with his game Vexicon being part of the 2012 Student Exhibition.
Project Roles:
Chris Elcombe:
- User Interface and User Experience design
- Server Development
- Public Testing and Public Relations
- Sketching and Prototyping
Patrick Reding:
- Narrative Design and Writing
- Engine Development
- Puzzle Design
Project Description:
Concept and Motivation
People like to learn, however, the manners in which students are taught may not seem interesting to them. To this end Untraceable is a 2D logic video game designed to teach high school students interested in programming and computer science an introduction to programming concepts and logic.
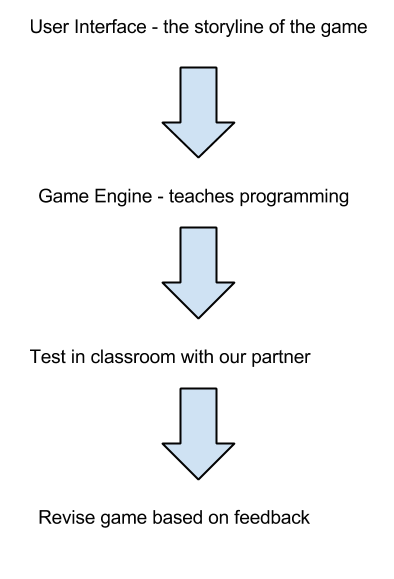
Methodology
Untraceable Plot Summary
Setting
A view of the city the game takes place in.
The year is 2024, and data rules the world. Our story takes place in a large Canadian city identical to, but not explicitly, Toronto. In light of revelations about NSA PRISM, world governments have been increasingly spying on their own citizens to “close the surveillance gap” with the United States, and Canada is no exception. While there was outrage at first, the years have led people to grow accustomed to the loss of freedom, Most people tell themselves that so long as there aren't secret police on every corner and people disappearing in night, everything must be okay. For them, life continues as it always has.
However, there are others that have more reason to fear for their privacy. A small percentage of humans are born with psychic abilities, usually manifesting around puberty. The vast majority are capable only of minor acts of clairvoyance and telepathy, though some have more dangerous abilities such as forcing their will on others. Since many of our social structures are predicated around people not being able to read minds, the consequences of releasing these individuals to the world would be unpredictable and dire. In Canada, keeping psions secret is the responsibility of CSIS's Central Psionics Unit (CPU). While it used to be that all but the most dangerous psions were publicly discredited, the “surveillance gap” led to the Untraceable Initiative: “recruiting” young telepaths to create data channels through the “mental fog” that permeates the world. This allow the CPU to transfer information without rival hackers being able to detect or decipher the information through non-psychic means.
It is for this reason our protagonist finds themselves being unceremoniously shoved into the back of an unmarked van on the way home from school.
Characters
The Protagonist:
Faceless, voiceless, and genderless, the protagonist serves primarily as a player surrogate. The only solid facts is that they are 16 years old, come from a loving middle-class family, and had no idea they were psychic before the abduction. Their power have been slow to develop, leading the CPU's psychic evaluators to rate them as a weak telepath. However, the protagonist is actually very powerful, able to steal and alter people's memories, which they learn to do over the course of the game. The protagonist's primary motivations are to escape from the facility, rejoin their family, and develop their psionic talents.
Agent Richard “Ritchie” Kernighan:
Kernighan is a CPU agent responsible for keeping and training recruits of the Untraceable Initiative. He is a caucasian male in his early fourties who is just beginning to grow bald. He is not actively cruel to his charges, but has little patience for anything that gets in the way of the mission, including emotions. He has especially little patience for One-One, insisting on calling her “Eleven” and tiring of her constant provocation. He sees the initiative as an unfortunate necessity to stop the more dangerous psychics from running amok. His primary goals are keeping his charges under control, completing the CPU's missions, and preserving national peace.
“One-One”:
Her real name is Ada King, although only she knows that. A 18 year old female, she became aware of her psychic abilities and the greater psychic community two years before the start of the game and ran away from home to avoid capture. She was found and captured six months prior to the start of the game, although the CPU did not link her to her previous identity. One-One is a minor clairvoyant, which allows her to receive and translate data packets from the mental fog, so she usually serves as the primary sink for the player's programs.
Her assumed name is the binary representation of the number three, making a pun on the word “free” to reflect her belief that knowledge grants freedom. A firm member of counter-culture, she is strongly opposed to authority and hates how complacent Canada has become to increased surveillance. She enjoys seeing how far she can push Kernighan, whom she always calls “Ritchie”. As the more experienced psychic, One-One takes on a big sister role to the protagonist, showing them the ropes, helping them develop their power and skill, and eventually using them to break out. Her primary goals are escaping from the initiative, rejoining the underground psychic community, and undermining the CPU.
Story Arc
Opening:
The protagonist awakens at the Initiative facility. Kernighan greets the protagonist coldly, explains the situation, and introduces them to One-One. One-One insults Kernighan, prompting him to leave them alone briefly to get to know each other. One-One expresses condolences for the protagonist's situation, and explains psychic powers and programs. Kernighan reenters, unapologetic for cutting the bonding short. Kernighan gives the player a tutorial mission, and he and One-One walk them through it.
Act 1:
The player completes missions for the CPU, sending information across the city. The protagonist learns how to route, pack, and unpack packets and use if statements. Eventually a mission requires the protagonist to find data that isn't actually present in the stream, whereupon they find they have the ability to manipulate data. Kernighan is unaware of how the task was accomplished, but One-One is. One-One urges the protagonist to keep this ability secret while encouraging them to use their power to undermine the CPU and look for information that may aid their escape.
Act 2:
Following One-One's advice, the player uses their data manipulation abilities to subvert the intent of the missions they receive. With One-One providing the written mission descriptions. The player learns to use advanced comparators, binary operations, and loops. The protagonist and One-One figure out that most of the data they are handling is being used to track and evaluate other psychics. They form a plan to alter the data to fake a massive incident that would require the majority of the CPU's staff to handle, giving them a window to escape.
Act 3:
The protagonist learns how to fetch data directly from people's brains, letting them steal building plans and access codes from guards. Once their plan is ready, the protagonist and One-One manipulate a warning system to fake a public attack by a group of powerful psychics. The player learns to handle strings, use assignment operations, and build a binary counter.
Once the coast is clear they make their escape, only to be stopped by Kernighan at the front gates. Desperate, the protagonist interfaces with Kernighan's mind, creating the final puzzle; where the player must sift out information pertaining to the CPU's operations.
Epilogue:
On the protagonist's success, Kernighan is helpless to stop his charges, but warns them against using the information they found to take down the CPU, as they are necessary to stop the most dangerous psychics from causing havoc. One-One is dismissive of this warning, and kicks him in the face before escaping with the protagonist.
Once they reach a safe distance, One-One informs the protagonist that it would be too dangerous for them to return home, and that it would be safer to stay together and rejoin the underground psychic community. Despite this being against the protagonist's wishes, they have to choice but to accept, with the hope that one day they may still return home.
High School Curriculum Summary
The following is a list of terms and concepts students should know, broken down by grade level. All of the following information is taken from the government curriculum found here, beginning at page 36 http://www.edu.gov.on.ca/eng/curriculum/secondary/computer10to12_2008.pdf:
Each grade level builds on the last, so only new concepts are listed in upper years.
Grade 10:
- data Types (ie numbers, strings)
- constants vs. variables
- order of operations
- assignment operators (a = b) and relational operators (a < b)
- boolean operators (AND, OR, NOT)
- store and manipulate data
- 2+ simple branching choices (if, if-then-else, if-then-elseif-else)
- simple loops
- trace simple programs
Grade 11:
- integers vs. float
- strings vs. 1D arrays
- boolean variables
- input processing
- nested structures (ie if() { if() {} } )
- subroutines, functions, and methods
- identify errors in code
- code validation through test cases
- flesh out code from a skeleton
- manipulate string data
Grade 12:
- data conversion (eg String to Int)
- code reusability
- sorting algorithms (bubble, insertion, and selection sorts)
- 2D arrays
- recursion
- comments and documentation
- work under a timeline
- encapsulation
- searching algorithms (linear, binary)
- read/write from/to external files
Initial Level Designs
Features/Tools:
- Source of data
- Sources of user generated psychic data
- Drain for data
- Trash for data
- if statements
- Pack data
- Unpack data
- spawn for data
Examples of What's in a Data Packet:
Data type and/or explanation in brackets
- name (string)
- address (mixed data represented as a string, eg 123 Somewhere Drive)
- phone number (numbers with delimiters ie 555-6789, “-” is a delimiter)
- job (string)
- age (number)
- psychic? (boolean with 3 answers: yes, no, undetermined)
- under government surveillance? (boolean)
Level Descriptions
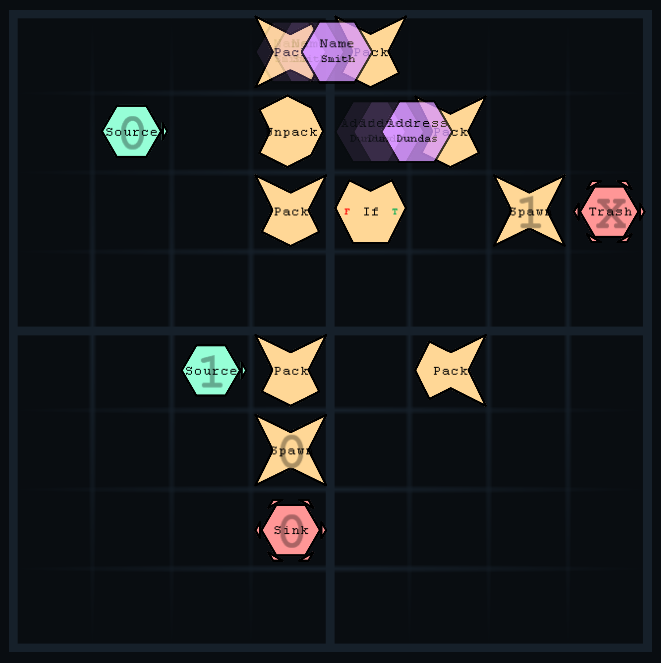
Example of level four being executed.
Opening/Prologue - The Tutorial Levels
After being captured, Ritchie and One-One show the user how to use their powers, and explain what the government expects of them.
1. Looking at working code in its most basic form.
- The user will be shown the different initial features
- See how they are used
- See how to attach features together
- See what is a valid final product
- Show source to drain flow of data
2. Replicate the Basic Level
- Users will be asked to create their own basic level
- Lets the user play with the features and create valid code
- Literally get data to flow from source to drain
- How to choose flow from a feature/tool
- How to comment code
3. Data examination
- Expand on the basic level
- Learn to unpack data to see inside
- Learn to repack data before drain
Act 1 - The First Assignments
After passing initiation, the user is given their first few simple tasks. Mainly dealing with organizing data in some way.
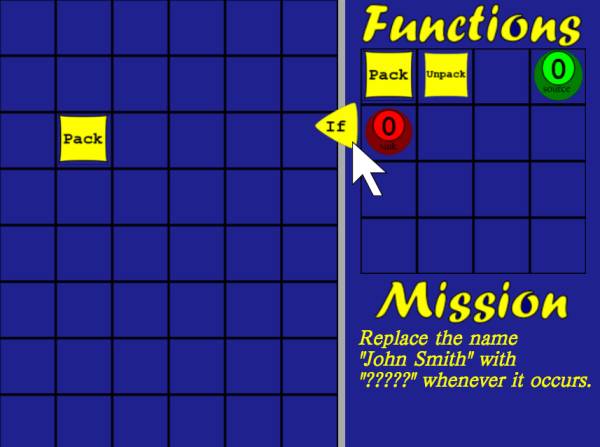
The government needs to quietly remove someone from the public eye, remove any data you find about person “Bob”. [Insert better name later]
4. The if statement
- Learn about the trash feature (gets rid of data)
- Learn about conditional statements
- Use these to remove all data on a certain target (ie if(name==”Bob”))
The government needs to compile a list of a specific group of people, only send to the drain psychics who aren’t currently under surveillance.
5. Joining conditions
- Learn about boolean structures (AND)
- Combine boolean conditions with if statements to narrow things further
The government needs you to add to the previous list anyone who has yet to be inspected and who is of age to have developed psychic powers (13-19 inclusive).
6. Joining conditions (2)
- Boolean structures (OR)
- Subroutines, adding to previous list (encapsulate this too in some way? Maybe a second source that is the list from last time that still needs to go to the drain)
- Boolean comparators (<, >)
7. Having examined your lists and the people attached to them the government needs you to update their database.
- Data replacement
- Given certain people change the status of whether or not they have psychic powers and if they are under surveillance (teaches assignment)
The government asks you to filter certain names out of the list pertaining to other psychics they’ve captured and are using. On completion the user discovers that One-One is not in the list. The user then discovers the ability to generate data and uses this to add One-One to the list, faking all her information.
8. Creation of Data
- introduce a new source for psychically created data
- learn how to integrate data from both the natural and psychic sources
Act 2 - The Escape Plan
At their next meeting the player tells One-One of their recently discovered power. One-One sees the potential to use this development as a means to escape their imprisonment. One-One tells them that around their normal missions they need to look up ways to ways to escape.
With ways of escape in mind, the protagonist decides to copy all of the data from their next mission, to sort the employees by job for an upcoming evaluation.
9. Multiple Data Drains
- introduce multiple drains for data
- each drain has its own conditions (eg here one needs sorted by job, other just needs raw data)
The government would like you to organize the new company list into alphabetical order. [used to be question 8 in Act 1]
10. Controlling multiple pieces of Data
- If statements would compare 2 pieces of data at once
- Only let one of them leave
- Counter/Null packet shows end of list (Teaches indexing)
- Repeat sort until nothing changes (Teaches loops)
- Teaches bubble sort
After the evaluation the company has decided to “end” the contracts of some of its employees. The protagonist is to remove anyone with this job title “terminated” and then resort the list by name.
11.Company Termination
- how to remove items from a list while keeping it sorted
After a minor hacking incident, some of the government data has been wiped. By comparing the hacked list to the backup file the protagonist needs to fill in the broken data in each packet. After completion the protagonist gets the idea for a mass incident that would lead the government on a chase leaving minimal security guarding One-One and themselves.
12. Data Recovery
- multiple inputs
- merge data into a single output
Act 3 - Putting the Plan into Action
The protagonist confronts One-One with the plan of creating a fake mass incident to create a situation of minimal security at the facility. One-One agrees but wants to make sure they work out the details of the plan before putting it into action.
Overhearing a conversation between two guards about the hacking, the protagonist attempts to listen in on the conversation. Doing this unleashes the power of the protagonist to read data from people’s minds. The protagonist then filters out all the information they can about the recent attack.
13. Getting Ahead
- Introduces the concept of data filtering from people’s brains into the protagonists’
- more of a plot device
Telling One-One of their new-found power she decides that they can use this power to steal the knowledge from the guards about the escape route and all the passcodes they’ll need along the way. [Note use the address and phone number fields to hold the location and passcodes]
14. Stealing the Plans
- filter through large amounts of information
- create more efficient searching methods
- order passcodes by location so you know the order to use them
With the plan ready, the protagonist inserts data into the system that tips off the government of a large number of psychics concentrated in an area known for resistance, forcing them to send a large number of agents to deal with the situation.
15. Tricking the System
- insertion sort for user generated data
- generate enough data to meet a threshold, but spread out to not look conspicuous to the system
After the system has been notified of the “impending” attack. The protagonist needs to implant a local emergency in the heads of the guards so that they leave the escape route clear.
16. Local Crisis
- insert a “thoughts” into the minds of the local guards until they feel the need to investigate
Having escaped the facility, the protagonists head towards the gate, only to be stopped by Kernighan. When he refuses to let them go and comes to the realization that they have created this situation, the protagonists decide they must wipe his memory to ensure their escape.
17. We Quit
- filter through the thoughts of Kernighan
- remove any memories dealing with: the CPU, One-One, and the protagonist
- keep and thoughts that the player feels might be useful
Epilogue
Having escaped the facility the two decide that the best plan is to stick together until the time that they can safely be reunited with their families and friends.
UI Images
Soundtracks
Looping soundtracks for the game have been designed to run in the background of the game. Unfortunately wiki pages don't let us upload the files directly for playback. They can however be downloaded here:
Narrative UI
Screen shots from the final version of the narrative of the game.
A movie of the narrative being played by a user before game integration.